 Take a look at our new paper, published at a recent issue of IEEE Software (Issue No. 01 – January/February; 2018 vol. 35), on how to coordinate cloud, fog, and edge computing. The paper was authored together with our colleagues at Electronics and Communications Engineering & Pervasive Computing, Tampere University of Technology, Tampere, Finland. The paper was It was a pleasure to work with our colleagues from Tampere, as always 🙂
Take a look at our new paper, published at a recent issue of IEEE Software (Issue No. 01 – January/February; 2018 vol. 35), on how to coordinate cloud, fog, and edge computing. The paper was authored together with our colleagues at Electronics and Communications Engineering & Pervasive Computing, Tampere University of Technology, Tampere, Finland. The paper was It was a pleasure to work with our colleagues from Tampere, as always 🙂
The core message of the paper is that as we approach novel techniques such as 5G, peer-to-peer radio technologies, and multi-access communication channels, we need new technologies that help us program the devices and their interactions in a simpler fashion. While we can work under the terms of different ‘islands’ of technology chosen for a particular application under normal condition, the ability to reach over the boundaries what was originally foreseen is an essential character at corner cases, in particular those that are of critical importance and whose failure or hijacking could lead to disasters.
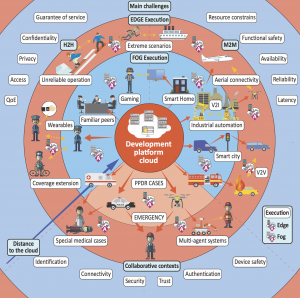
Considered application scenarios of Cloud, Fog, and Edge computing for the AcOP model. H2H = human-to-human, M2M = machine-to-machine, PPDR = public protection and disaster relief, QoE = quality of experience, V2I = vehicle-to-infrastructure, and V2V = vehicle-to-vehicle.
Author’s post-print version (pdf), which in is content equal to the fully formatted, published version available from IEEE