All devices connected to the Internet are susceptible to online attacks. Attacks make use of security gaps in software and devices, as well as the gullibility and carelessness of web users. Scams and attacks may have serious consequences, so being protected against them is important.
The reasons for the attacks may include:
- vandalism: security breaches may involve stealing and deleting files
- political reasons: the attacker may use a computer to conduct a DoS (Denial of Service) attack. DoS attacks aim to prevent or slow down the operation of a service.
- money: the attacker can earn substantial amounts of money by turning your computer into a server that sends out junk mail.
- piracy: the attacker can utilise the web for distributing files illegally.
Social engineering
Social engineering means that the scammer persuades somebody to hand over passwords or similar information that allow the scammer unauthorised access to an information system. An example of social engineering:
One day, a person posing as an IT administrator at University of Helsinki called a friend of Raymond’s, Charlie. The caller claimed that Charlie’s e-mail was stuck and he would have to give them the password to his e-mail. Charlie provided the password and, not long after, he received another phone call. This time, it was the police. Charlie’s password had been used in a scam operation with the aim of leading the traces of the operation to Charlie and not the actual culprit. After extensive explaining, Charlie managed to convince the police of his innocence, but the episode left a bad memory and a suspicion towards phone calls from unknown callers.
Scam messages
The Internet is full of scamming operations of various levels of complexity, such as phishing, Nigerian scams, and prize draw and lottery scams.
Phishing
The aim of phishing is to persuade web users to give up personal information through a fake website. Online banking services are often the target of this kind of scam.
Charlie received mail that seemed to be from the online service of a certain bank. The message requested Charlie to provide his username and the related key codes. The message contained a link (By clicking this link you can read the whole message.) that seemed to lead to the bank’s website. However, Charlie thought the message might be a scam: he had heard that banks never request your user information by e-mail. Furthermore, the link did not go to a domain-name address (DNS) but to a cryptic IP address:
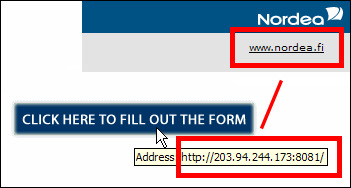
Charlie decided to investigate the matter, so he opened the website (click here to see the picture of the scam page). His suspicions were confirmed when the website asked him to provide his username and several related key codes. Charlie decided to call the bank and inform them of the scam attempt. The scammers were caught and sentenced to jail.
If you suspect that a website is a scam, check its address: you can view the URL of the link by placing the mouse cursor on the link (see the picture below). This will bring up the real URL of the link (usually displayed at the bottom of the browser or e-mail client window). Be careful not to accidentally click on a link. If the link shows something not mentioned on the page, you have reason to suspect its authenticity!
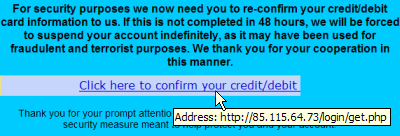
Reading the address carefully even when it does not seem cryptic is important, as scammers count on people being careless. Compare the following addresses: the first could be genuine, and the one below the address of a fake website:
www.netwallet.com
www.netwallet-admin.net/a/b/c/login.php
Many scammers try to make you log in through the links they send, so be careful regarding all messages asking you to log in. Many scams try to make you check e.g. online banks, money transfers, or auctioned objects.
A significant number of all scammers try their best to have you sign in through the links they send you, which is why you should always be very careful when dealing with messages that require you to sign in somewhere. Quite often, scams involve requests to review information concerning online banking, money transfers or auction items.
Nigerian letters and other advance-fee scams
Nigerian scams are another common type of online scam. They all follow the same pattern: a great sum of money will be paid to you if you can simply offer a small sum to help the owner of the money transfer their money from one country to another. Typical features of Nigerian scams:
- the message comes from a stranger or an unfamiliar company
- the home country indicated in the message is a country in Africa or Asia that has been “going through a rough time”
- the message requests monetary aid and promises substantial amounts of money as reward
Read the Nigerian letter that Raymond received in his mail.
Lottery and sweepstake scams
A third, fairly common type of scam are the lottery and sweepstake scams. The common denominator for these messages are:
- the messages announces that you have won a large sum in a lottery you did not know you had participated in
- the letters are usually in English
- the letter may start with the words Confidential, Claim your prize, Urgent etc.
- the letter advises you to keep it secret
- the letter tries to persuade the user to give their e-mail address, for example.
The purpose of lottery and sweepstake scams is usually to gather e-mail addresses, which will later receive junk mail. E-mail addresses are bought and sold, so DO NOT reply to such messages!
Read a lottery scam that Raymond received.
Lottery and prize scams
The third common type of scam comprises lottery and prize scams. This type of scam message often includes one or more of the following features:
- the message informs you of a great win in a prize draw that you did not know you participated in
- the message may begin with words such as Confidential, Claim your prize or Urgent
- the messages try to get the user to provide information, such as their e-mail address
The aim of lottery and prize draw scams is usually to collect e-mail addresses to which junk mail can be sent later on. E-mail addresses are bought and sold, so never reply to these messages!
Read more about the lottery scam message Raymond received among his mail.
Hoax messages
Hoaxes are fake warning messages normally distributed by e-mail in the form of a chain letter. A hoax might contain a fake virus warning that advises you to forward the message to your friends and acquaintances.
Reading and processing hoaxes takes time and storage space, thus causing considerable load to both servers and their users. Sometimes the instructions in hoaxes can even lead to users doing harmful things to their computers. Always proceed with caution when you encounter a chain letter: do not forward hoax messages or reply to them!
You should close pop-up windows and advertisements that contain warnings. Do not click the OK text or other buttons on the windows: they will likely just open more scam windows or take you to a scam website.
Blackmail scams
Blackmail scams are a fairly typical subset of online scams. Blackmail scams often claim that the sender of a message has somehow gained access to the recipient’s device and sensitive information they contain, such as nude images.
Typically scammers will blackmail the victims to pay them with Bitcoins, threatening to otherwise publish the alleged information.
Almost always these messages are pure intimidation, and no remote access to the computer has been established and no sensitive recordings exist.
If, despite everything, you notice that you have become the target of an online scam, immediately change your password on the university’s password change page and contact IT-Helpdesk!
The information security specialists at the University of Helsinki have compiled examples of typical scam messages designed to obtain passwords, money or personal data from university staff and students. The list can be found in Flamma.
In order to strengthen information security awareness and reduce the risk of online scams, the University of Helsinki has introduced an annual IT Security Test for University staff and students. The test for degree students was introduced in phases from February 2022 onwards. More information about the test and instructions for its completion are available in Studies service.