Malware
Viruses and spyware are some examples of malware (malicious software) that can cause a great deal of damage if they invade your computer. the damage is caused both to the owner of the infected computer and other users, so it is very important to protect your computer against malware.
Viruses
Viruses are malware that spread from one computer to the next by attaching to a file. The virus can damage hardware, software or files. Some viruses are merely annoying, but others can cause real damage; they can delete files that are important for the computer to function, for example. You can affect how viruses spread, because viruses do not spread without human assistance. The simplest way to prevent viruses from spreading – and your own computer from being infected – is to always scan any files you receive or send for viruses.
Worms are malware that spread on their own and send perfect copies of themselves over the web. This means that a computer that has been infected with a worm will try to infect other computers on the web, by resending itself every time the computer is turned on. Worms usually spread very rapidly, since they can send themselves to all the addresses in the address book in your e-mail program, for example. Worms can also block the entire web traffic of an organisation as it advances like a chain reaction.
Trojans or Trojan horses are computer programs that are spread along with other programs that seem useful. Users are tempted to open the program containing a Trojan with their own computers so that the feature hidden in the program can infect the computer. When this is done, crackers can find infected computers with their own programs and take over the control of an infected computer with the aid of the Trojan. Then they can, e.g.:
- copy and destroy files
- read passwords, e-mail and banking information that has been stored on the computer
- send junk mail in the name of the victim
- spy on the user
- load more Trojans or viruses to the computer
Viruses often spread through e-mail; the virus is activated when you open an attachment (usually by double-clicking on the attachment icon). Some viruses spread through programs that can be downloaded from the Internet or from storage media that have been used in infected computers. Protect your computer with an anti-virus program!
Spyware is software that is designed to spy on you and what you do. Spyware can observe which files you edit on your computer, for example, or which web pages you visit. The program then sends this information to an address specified in the spyware. The information is then used for marketing or sending junk mail.
Ransomware is malware that, once installed on a computer, requires the user to pay a ransom to unlock the computer. There are two different types of ransomware: the first will actually encrypt all or part of your computer’s hard drive. The second type of ransomware are called scam malware, meaning they do not actually encrypt any files on the computer, but only notify the user computer about the files having been locked and demanding a ransom payment. If you find your computer is exposed to ransomware, never pay the ransom and contact Helpdesk.
One day, a platonic friend of Raymond’s, Gunilla Parmesan, told him that every now and then, obscene adverts would appear on her computer screen. When Raymond started to clear up the problem, Gunilla told him she had used a P2P program to cunningly and illegally download the music of the Finnish-Swedish band Pent. It turned out that a spyware application had been downloaded along with the program. It took a long and hard cleaning procedure to rid the computer of the spyware, including removing the P2P program.
Protection against malware
You yourself are the best prevention against spyware, because you are the one who decides what to install on your computer and what you do with it. Common sense is the most important thing, and to be aware of the ways in which malware can access your computer. Follow the directions below to prevent spyware from invading your computer.
- Beware of program files in your e-mail: whenever you receive an e-mail attachment, make sure that it is not a disguised program file! The message that is sent with malware is often written in a way that is meant to tempt you to open the attachment. Files like this are often named something else than what they actually contain, e.g. a picture for you, a flight ticket or instructions on how to cash a large sum of money, but in reality are something completely different. You can identify malicious program files in Windows by looking at the file extension: dangerous file types include EXE, COM, BAT, CMD, SCR and PIF. The example in the image below contains malware: the attached file has two extensions, and the latter, i.e. the real file extension, is a dangerous SCR.Due to virus risks several mail servers do not let certain dangerous file types through at all. The senders of malware can get around this by packing the files, which also changes their file extensions.
- Disable the use of HTML in your e-mail program: malicious program code can also be written into a normal e-mail message body. In such cases the message is usually sent as HTML. When you open the message or view it in the preview window, the program executes the program code in the message. It is better to use a TXT type preview feature in your e-mail program (read more about this subject).
- Do not browse suspicious-looking web pages or click on every link or advertisement on a web page: malware can also be hidden on a web page, so that merely visiting the page may bring the malware to your computer. A web page can also contain a link to malware; when you click on the link, a file with the malware is downloaded to your computer. If you wish, you can make the information-security settings for your browser stricter (read more on e.g. the support pages of the Firefox browser).
- Make sure that the program installation discs and files that you use come from reliable software manufacturers: malware may also come with an install disc for a program. A typical example is an pirate program file containing malware downloaded from a P2P-network. Be careful and buy your programs from reliable sources!
- Don’t insert unknown USB flash drives! Criminals can leave USB sticks loaded with malware or machine-cracking circuits as bait in public spaces, trusting that someone will, for their goodness sake, find out their owner.
- Remember to act securely with your phone! An unprotected mobile wallet, proximity reading features and a lost or stolen phone are a really bad combination. Find out more about the secure use of smartphones on IT-Helpdesk’s instructions.
It is a good idea to keep file extensions (read more about them in chapter Properties of files and directories) in view always, since malware that is spread through e-mail attachments relies on people not seeing the difference between the real extension and a fake one! Dangerous extensions are usually masked with two different extensions to fool the user into thinking the message is safe. Keeping the file extensions in view and keeping an eye on them will diminish the risk of opening an attachment containing malware.
Using computer security programs
Computer security software will protect your computer against viruses, worms, Trojans and many other kinds of malware that can be transmitted by diskettes, CDs, DVDs, USB sticks, and your Internet connection. Most computer security software work according to the same principle; whenever you connect to the Internet, the program will update its virus list.
Virus lists are maintained by the manufacturers of the software, listing known viruses and malware. As long as the virus list of your computer security program is up to date, your computer is fairly well protected against threats. However, since new viruses are created all the time, even the best computer security programs may not find the latest ones. Having an computer security program running and updating its virus list are only a couple of measures with which you can improve your safety – they do not diminish your need to be careful.
Computer security programs have so-called run-time virus control checking your computer’s file system actively all the time. When it finds a virus, the program will warn you with a pop-up window, where you can select to remove the virus from the file – or even to delete the whole file. Be careful when you respond to the program.
Scanning files for viruses
It is best to save files that you get through e-mail or download from the web onto the hard drive before opening them, so that you can let your computer security program scan them for threats. With most programs, you can start a virus scan by clicking on the file with the secondary mouse button and selecting the command Scan for viruses or similar – depending on which program you are using – in the menu that opens on-screen. Some computer securiry programs scan attachments automatically when you open it from the e-mail program, but if you are not sure about how your computer security program works, do not risk it, but always scan attachments etc as described above.
What to do when infected with a virus
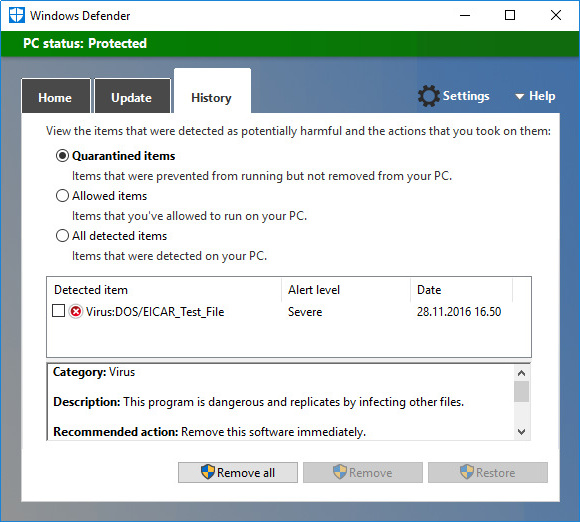
If a file has been infected, the computer security program will usually inform you and tell whether it has been able to erase the virus automatically. However, sometimes the computer security program leaves it up to you to decide what to do about the infected file. If the file is not important, simply delete the whole file. If it is an important file, try to disinfect it. The disinfection does not always work, or the file may be damaged in the process, so keep in mind the importance of back up copies! The image below shows a warning from an computer security program; the program has discovered and deleted a test virus called EICAR.
There are two different computer security software in use at the University of Helsinki. The first one scans all incoming mail for viruses before sending it on to your mail inbox. In addition, UH-owned computers are protected by computer security software.
Updating the virus list
Most computer security programs update their virus lists automatically. However, you may sometimes need to update it manually, e.g. if you want to make sure that you have the latest version of the virus list. Most computer security programs have a feature called something like Update now for updating the virus list.
Scanning your whole file system for viruses
Earlier, we described the run-time virus scan that will protect your computer from viruses. In some situations, you may want to run a complete virus scan of the storage units on your computer (such as the hard drives and USB memory sticks). Some examples of such situations:
- Scanning the computer after installing a new computer security program: upload the newest virus list directly after installing the program and scan all hard drives and other storage media connected to your computer.
- Discovering a virus: after removing a virus that was discovered during run time, it is best to make sure that all copies of the virus have been removed from the file system.
- Suspicion of a virus: if you suspect that there is a virus in your computer, download the latest virus list and scan your whole computer for viruses. If necessary, check the web site of the manufacturer of your computer security program whether a new virus has been discovered that has not yet been added to the virus list.
Firewall – the gatekeeper of your computer
How do the search requests you give your web browser know how to bring back the web page you want to your browser? Pages can be retrieved from the web because the Internet traffic (IP traffic) on your computer is directed to your programs through something called ports. Different programs reserve different ports for their own use as ‘return addresses’ so that no other program can use the same port at the same time.
The ports exist in code, not as actual physical ports. Due to programming errors, the ports may contain security holes, which may allow sniffers to enter the computer through the ports – unless the ports have been protected with a sort of ‘gatekeeper’ program. This guard of network traffic and computer ports is called a firewall.
Using a firewall
The firewall program closes every port in the computer from unauthorised use. When the ports are closed, you computer is fairly secure from inbound contact attempts, but programs cannot access the web, so you have to give your programs permission to do so. This means that you have to decide which programs are allowed to access the web and which programs may receive inbound traffic.
The firewall will usually ask for your permission for Internet traffic with a dialog box like the one shown below. The dialog boxes vary according to program, but they usually contain the following information:
- The direction of the contact request: is the contact request made from your own computer (outbound traffic) or to your computer (inbound traffic)?
- The IP addresses of the requests: local IP means your computer’s IP address, remote IP is the IP address of a server.
- Information on the program that is requesting contact: if you install a new program that uses the web on your computer, the firewall will send you its request for a network connection, which you have to allow or deny.
Read each request carefully and consider what the firewall notification is about. Do not click on the Allow and Deny buttons on the program at random: with a firewall, you have to know which kind of traffic to allow and which not!
You should not automatically allow all outbound traffic, nor should you automatically deny all inbound traffic. The firewall is completely worthless if you allow all the traffic without any deliberation.
Even though it may prevent some malware from accessing your computer through ports, the firewall is not an computer security program. To protect your computer from malware, you should also install an computer security program in addition to a firewall.
Where do I get a computer security program?
You can buy an computer security program from software stores or e.g. through your Internet service provider (ISP). Many free computer security programs can also be found on the Internet. Many such software include a slightly more advanced firewall.
F-Secure offers students at the University of Helsinki the SAFE software at a student-friendly price. Instructions for purchase and installation can be found at the IT Helpdesk info site.